- home
- articles
- quick answersQ&A
-
discussionsforums
- CodeProject.AI Server
- All Message Boards...
- Application Lifecycle>
- Design and Architecture
- Artificial Intelligence
- ASP.NET
- JavaScript
- Internet of Things
- C / C++ / MFC>
- C#
- Free Tools
- Objective-C and Swift
- Database
- Hardware & Devices>
- Hosting and Servers
- Java
- Linux Programming
- Python
- .NET (Core and Framework)
- Android
- iOS
- Mobile
- WPF
- Visual Basic
- Web Development
- Site Bugs / Suggestions
- Spam and Abuse Watch
- featuresfeatures
- communitylounge
- help?
Everything / Security / Encryption
Encryption
encryption
Great Reads
by Kashif.Mushtaq.Ca
Cross Platform AES 256 GCM Encryption and Decryption (C++,
by Clark Fieseln
Compress,
Latest Articles
by Wessel Beulink
What is Azure Virtual Network Encryption? Azure Virtual Network encryption provides a layer of security that encrypts virtual network traffic,
by Federico Di Marco
Fededim.
by Federico Di Marco
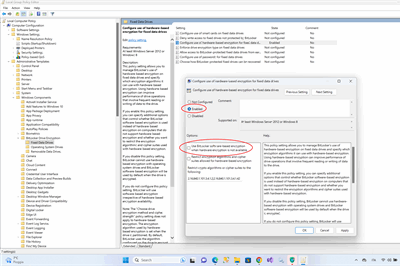
How to enable Bitlocker hardware encryption on self encrypting drives
by adriancs
Communication between Arduino and C# (ASP.
All Articles
29 Nov 2017 by
9 Jun 2023 by Kashif.Mushtaq.Ca
Cross Platform AES 256 GCM Encryption and Decryption (C++, C# and Java)
25 Sep 2021 by Clark Fieseln
19 Feb 2022 by Asif Bahrainwala
10 Mar 2018 by Joe Dillon
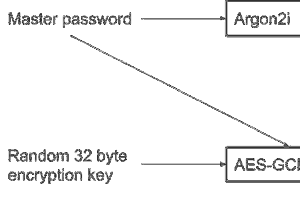
This article describes the security techniques required to create a secure offline password manager and how the Libsodium library has been used to achieve this. YAPM stores passwords with AES encryption and authenticates users with an Argon2 hash.
22 Dec 2023 by Federico Di Marco
How to enable Bitlocker hardware encryption on self encrypting drives
20 Dec 2010 by OriginalGriff
There are a couple of things here:Normally, you would use String.Split, but there is no overload which splits on a string, so the direct answer is to use the Regex.Split function:string myString = "xhsdg495 - jasjdhfb";string[] parts = Regex.Split(myString," - ");parts[0] is...
20 Feb 2011 by Jammer
16 Mar 2011 by #realJSOP
The answer to your question is YES. There are 3rd party libs abvailable, and some open-source stuff. Learn the power of google, and all will become clear.
3 Aug 2012 by Kenneth Haugland
25 Apr 2014 by KarstenK
10 Nov 2018 by DataBytzAI
19 Aug 2023 by adriancs
7 Feb 2024 by Federico Di Marco
Fededim.Extensions.Configuration.Protected is an improved ConfigurationBuilder which allows partial or full encryption of configuration values stored inside any possible ConfigurationSource and fully integrated in the ASP.NET Core architecture using Data Protection API.
17 Mar 2011 by OriginalGriff
Password strength is a complex subject.Technically speaking, a random password with a mix of upper- and lower- case alpha, numerics and special characters is the strongest.However, if the user cannot remember it, then he will write it down - normally on a post it attached to teh...
25 Jun 2013 by Abel Wike
8 Sep 2014 by cogi83
A SW to send your WAN IP and other info via email
7 Dec 2016 by Kuv Patel
Decrypt Stored Procedures, Views, Functions, and Triggers in SQL Server
8 Nov 2018 by DataBytzAI
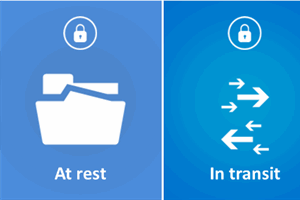
Overview of encryption at rest, in motion and in use with Azure Encryption
19 Jan 2011 by Nish Nishant
See http://msdn.microsoft.com/en-us/library/aa375685(VS.85).aspx[^]Based on that 0x80880283 is CAPICOM_E_ENVELOP_RECIPIENT_NOT_FOUND. More details:The recipient cannot be found in the EnvelopedData object. Usually, this does not happen with an EnvelopedData object that was created...
28 Mar 2011 by OriginalGriff
Why not use the .NET implementation of the various encryption / decryption algorithms?See the System.Cryptography Namespace[^]Consider TripleDES encryption[^] - there is an example of how to use it in the link.
9 Apr 2011 by Albert Holguin
that's quite a project... controlling a UAV through a 3G modem seems like it wouldn't work very well... what happens if you drift out of reception range? you'll lose the aircraft and all the equipment, this isn't the type of project that someone can do on their own with limited budget.
8 Jun 2011 by Sergey Alexandrovich Kryukov
I'm not sure, but I feel you're missing the very essence of Public-key Cryptography.See http://en.wikipedia.org/wiki/Public-key_cryptography[^].Now, read my lips: you always encrypt with one key and decrypt with another one.See...
12 Sep 2011 by Ronald L
Hello Everyone,I have a question regarding the actual signature value on a X.509 v3 certificate. According to the recommendations stated in RFC 2459 and RFC 3280, the signature value should be located immediately after the signature algorithm. But all the certificates in my certificate...
30 Dec 2011 by OriginalGriff
Encryption does not look at encoding - it works on a stream of bytes, and does not assume any encoding at all. If you think about it, that is the only way it can work, unless the encryption algorithm is told "this is a binary executable file, treat it differently" which would be counter...
3 Aug 2012 by Sergey Alexandrovich Kryukov
Decryption of a password is never needed. And no one is supposed to know any passwords, no matter how much permission a person has. Only one person in the world should know the password: the owner of it, the one who created a password.You may ask, how authentication is possible then? Well,...
1 Jan 2013 by Karl Stoney
In this post, I will show you how to handle automatic encryption and decryption of hidden form fields using Rijndael.
30 Apr 2013 by Farhan Ghumra
3 Jun 2013 by Zoltán Zörgő
I assume you didn't visit google in this topic... pity :(http://www.dreamincode.net/forums/topic/156922-aes-encryption-and-c%23/[^][update]This is working for me:string decrypt_function(byte[] Cipher_Text, byte[] Key) { RijndaelManaged Crypto = null; ...
30 Jun 2013 by Sergey Alexandrovich Kryukov
Nobody is supposed to "recover a password", otherwise it would defeat one of the most important properties of the passwords. Passwords should not be recoverable, ever. If a password is lost, a brand new one should be created. I would say, the major purpose of password recovery would be...
15 Aug 2013 by OriginalGriff
MD5 is not an encryption algorithm - it is a hashing algorithm. The big difference is that encryption can be reversed, hashing can't. So once you have hashed your password (combined with the challenge key in some way) your password cannot be derived from the information you share with the...
3 Oct 2013 by Dragonranger
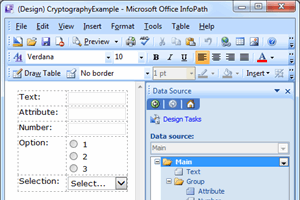
A neat library which can be used to easily add encryption for InfoPath form data.
1 Feb 2014 by OriginalGriff
The chances are that it isn't encrypted - it's just plain wrong, or it's binary information.Look at the documentation for your scanner, and see what it says it produces, and how it expects the interface to be configured - your use of "COM port" implies it's a rather old device, which would...
21 Apr 2014 by OriginalGriff
Encryption always produces "special characters" because it converts the input (from text or whatever it was) to a collection of bytes - which aren't characters, they are eight bit values which may contain valid characters but are more likely not to.Try converting the byte array to Base64[^]...
2 Mar 2016 by OriginalGriff
No.Youtube uses encryption because it's T&Cs prohibit downloading.And as Sean has already told you regarding your tip on the subject, we do not support anything which contravenes another site's T&Cs.
31 Jul 2016 by OriginalGriff
Check your data: When I copy and paste your code and data: private void butTestIt_Click(object sender, EventArgs e) { string str = "rb3Cmy54Q8sANMHkelt9QzqOnM3enifu6v7AG5567oiqDk5ijwSwcSzfxUgHm4xD"; MemoryStream ms = Demo(str); } ...
16 Oct 2016 by Z Kavtaskin
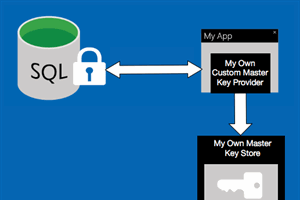
How to create a Custom Key Store Provider for SQL Always Encrypted (Without Key Vault Example PoC)
22 May 2018 by OriginalGriff
We cannot help you, and we would not if we could. Your free licence was for one year, and that has expired. You no longer have the rights to play the videos without purchasing a new licence from the original manufacturer. Any attempt to break the encryption with be in breach of your licence,...
2 Nov 2018 by OriginalGriff
You do realize that won't work? There are a couple of reasons: 1) If the code is exactly as you show, then the output of the encryption method will be all '*' characters - and you cannot under any circumstances decrypt that to get the original input. 2) If you have replaces the characters you...
14 Dec 2018 by OriginalGriff
No. You can't encrypt data into a fixed size at all, and particularly not into a small number of bits: if you could, why would we stream movies as 10GB lumps, web pages as huge chunks of "text"? We'd just encrypt them to 24 char alpha values and send that instead. Why would we store files on...
3 Jun 2019 by OriginalGriff
Yes ... but it's not a good idea. Remember, Javascript is interpreted in the browser - so the full code is sent to the client in a human readable form, which can be viewed in detail by anyone with access to an F12 key. So static salt in JS is pretty much the same as "no salt" because it is...
14 Aug 2023 by Daniel Ramnath
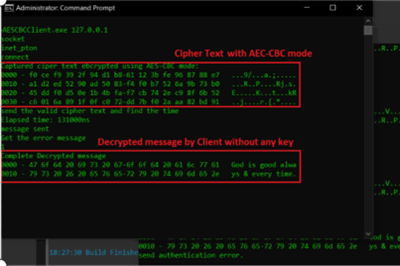
C++ OpenSSL 3.1 Attack AES-CBC using Padding Oracle Attack, and Timing Attack
8 Mar 2024 by Pete O'Hanlon
As you have deduced, the database encryption SDK applies at the database itself. If you were looking to apply searching through OpenSearch or ElasticSearch, you wouldn't be able to search these fields there. If you're searching on the DynamoDB...
8 Mar 2024 by Patrice T
Quote: Let’s say we want some sensitive properties, in one of our data structures, to be encrypted but at the same time it’s key that information is still searchable by the right recipient and here lies the origin of our research. As far as I...
Where is a good place to go to find people to test software I made before deploying it in my office?
27 Aug 2010 by Christian Graus
Surely the people in your office who will use this program are the best people to test it, as they know what they want it to do, and they are the only ones who can test their ability to understand your UI ?
18 Dec 2010 by LoreP21
I answer myself:I don't need to transfer bytes from the decrypted stream to a new stream, and then deserialize the new stream. It's enough to initialize the cryptostream in read mode and to deserialize from it:In = new System.IO.FileStream("[Removed path]", System.IO.FileMode.Open,...
16 Feb 2011 by E.F. Nijboer
Maybe bitlocker to go is something for you. Have a look here:http://www.techrepublic.com/blog/window-on-windows/secure-your-usb-drives-with-bitlocker-to-go-for-windows-7/1176[^]Good luck!
15 May 2011 by kastriotlimani
I have a project to implement use of s boxes of DES (data encryption standard) in win form application ..if anyone can help me with some ideas or hopefully to tell me some useful lines of code that would be helpful to me ... ps: I don't need all the des algorithm , just how s boxes work...
26 Oct 2011 by CPallini
The problem is (I suppose) the lineRijndael RijndaelAlg = Rijndael.Create();It generates a fresh key everytime is called. When you need to decrypt a previously encrypted file you must provide exactly the same key used for encrypting it.
26 Oct 2011 by Jürgen Röhr
Hi,at the start of your program you create a new Rijndael-instance and use it's key and iv for en-/decryption. Thus, when you go through both functions in THE SAME run, you use THE SAME key/iv-pair for en- and for decryption.If you go through them separately, you use different...
27 Oct 2011 by Pete O'Hanlon
There's no way to do this with standard FTP, but you may be able to use FTPS - assuming that the site you are trying to connect to supports it. Basically, you can think of FTPs as being the FTP equivalent of HTTPS; in other words it uses SSL for file transfer.There's a demonstration of doing...
4 Nov 2011 by Richard MacCutchan
It could be anything; since it is encrypted there is no way of knowing. After all, if it was easy to discover what it was it would not be very secure.
23 Nov 2011 by Menon Santosh
24 Feb 2012 by Perić Željko
Hello ,this is my solution for JoeilG ,first browse in the CodeProject under Learning Zones , Solutions Center , General Programming, Cryptograpfy & Security you have a whole chapter devoted to cryptography. http://www.codeproject.com/KB/security/[^]Here is sample of code...
4 Dec 2011 by Dalek Dave
This is an English Language Site.All the comments in code are not much use to non-German speakers.May I suggest a few minutes of your time translating them may be useful.
30 Dec 2011 by Andreas Gieriet
Hello Hassan,Is this what you are looking for?You may exchange alg and the associated aux functions to match your needs.If you have a byte array instead of a C# string, you may leave away the Unicode conversions to byte array.If you do not need a printable representation, leave the...
6 Jan 2012 by julian@giant
HiWe have implemented a web site with a SQL server backend database. We have used symmetric column encryption in the database. The stored procedures open and close the key prior to any read or write.All this works very well indeed, and we can see that all the data is beautifully...
19 Jan 2012 by Simon Bridge
I have a question for all those security boffins out there.I am developing a Tcp/Ip based client/server system that needs to be VERY secure.I'd like to know if there are any obvious vulnerabilities in the way the system works.Each communication is initiated by the client, the server...
1 Nov 2012 by OriginalGriff
Binary, octal and hex are all the same in this context - you just need to convert the string to bytes:string s = "Hello!";byte[] bytes = System.Text.Encoding.ASCII.GetBytes(s);
26 Nov 2012 by Palavos
3 Jan 2013 by YvesDaoust
I'd like to be able to copy unencrypted files from a disk to an external storage (whatever kind), and then back. I would like that when copying to external storage, the files transparently get encrypted, and when copying from external storage, they get decrypted. This way, I'll see no change on...
3 Jan 2013 by Sergey Alexandrovich Kryukov
Let me tell you that this is nasty. I would advise you to think and weight million times before you decide to introduce such a draconian limitation on your users. Think is your video is really that valuable that anyone would want to steal it. :-)Let me also tell you that, in principle, given...
25 Jan 2013 by Zoltán Zörgő
You mean NTFS encryption[^]? Forget it, you won't be able to decrypt it in a reasonable amount of time (several years).To avoid such situations in the future, I suggest you study this article really carefully: http://technet.microsoft.com/en-us/library/cc512680.aspx[^]No, actually you...
13 Mar 2013 by Shubham Choudhary
Hi!!! 1. for this you want to firstly encrypt your web.config file text!!!/*-------------------------------------------------------------------------------------*/ /*Encription of Web.Config*/ /* private void EncryptAppSettings() { Configuration objConfig =...
26 Apr 2013 by StianSandberg
Rijndael/AES is a block cypher. It encrypts data in 128 bit (16 character) blocks. Cryptographic padding is used to make sure that last block of the message is always the correct size.You need to explicitly set the padding for both encryption and decryption.For example: mainRM.Padding =...
2 Jun 2013 by AlphaDeltaTheta
DES is a block level cipher. You must use a padding mechanish such as CBC,CFB8, OFB8 or PKCS5 etc.
10 Jul 2013 by Thanks7872
Refer these links.Use SFTPBlackbox from C# .NET to upload and download files via SFTP (SSH File Transfer Protocol)[^]SecureFTPConnection Class[^]Chilkat FTP-2 .NET Component[^]sftp client code in C# without using any dll[^]An FTP secure client library for C#[^]Regards.....
28 Jul 2013 by Dholakiya Ankit
5 Nov 2013 by Sergey Alexandrovich Kryukov
As this is Windows, you can use Win32 Crypto API: http://msdn.microsoft.com/en-us/library/Windows/desktop/aa380255%28v=vs.85%29.aspx[^].This CodeProject article could be useful: Encryption using the Win32 Crypto API[^].I would understand if you prefer some open-source implementation....
3 Dec 2013 by Mehdi Gholam
Yes it is possible through brute force but it is not probable.You are advised to stick to the RSA guidelines on publishing and securing keys and not deviate.
24 Jun 2018 by Alvan Khong
I've created a login page with some simple SQL query function & i'm trying to encrypt my URL query string, but it seems there's some problem with it, everytime after i used my "button" function the URL reveals itself. May i know what's the problem with me coding? Remark: I've putted...
6 Mar 2014 by OriginalGriff
No. We do not condone, support or assist in the production of malicious code in any way, form or manner. This is a professional site for professional developers. If you want to know how to create such things, you need to visit a hacking site: but be sure to disable all firewalls and...
18 Jun 2014 by phil.o
I don't get you : a text encoding is not, in any way, a cryptographic algorithm; a text encoding represents the way the computer stores the bytes representing a text.Changing an encoding is as trivial as byte[] originalBytes; // Here the sequence of bytes representing the UTF-8 encoded...
28 Jun 2014 by JayantaChatterjee
Hi, I want to Encrypt and Decrypt plain Text with C# with different keys.When I run this code its gives the error Invalid length for a Base-64 char array on rijndaelCipher.Key = Convert.FromBase64String("ABC");I also tried rijndaelCipher.Key = Encoding.ASCII.GetBytes("ABC");// but it...
2 Jul 2014 by CPallini
Please check your code. I copied the example in this MSDN page: "MD5 Class"[^], changed the input string from "Hello World!" to "123" and eventually got the correct result.
17 Sep 2014 by Dennis E White
Not really an answer but more so an explanation. You can do all sorts of tricks to make it hard for someone to view the page source but the bottom line is that because this information is coming across as plain text there is nothing you can do. Anybody determined enough to view the source on...
17 Sep 2014 by Sergey Alexandrovich Kryukov
If a user can see your page, its source is already on the client side. Too late to try to hide anything.Face it: if a browser can interpret/render some your resource from the source data, the user can do it, too.—SA
15 Jan 2015 by Zoltán Zörgő
The url you have does not need encoding. Please note that URL encoding has nothing to do with encryption - it encodes special characters to pass http traffic correctly. I have a feeling, that you want something else. A page itself can't be encoded. Redirection happens on client side based on a...
29 Jan 2015 by TheRealSteveJudge
You asked for encryption and do not seam to care about decryption.In this situation there is a quite simple way to createa random encryption key:string encryptKey = Path.GetRandomFileName().Replace(".", string.Empty)More information can be found...
20 Feb 2015 by OriginalGriff
"Dr.Kawashima" is a commercial product - a series of "brain trainign" games - and the only obvious reason for decoding the profile save files is to alter them to give yourself a "better" rating.This is not something that we get involved in as a site: it's technically malicious code as it...
15 Mar 2015 by OriginalGriff
1 Apr 2015 by OriginalGriff
If they provided the key, and the software to use it, then you need to talk to them.We have no idea what they gave you, and one or both of them could be wrong. Only they will have the records to know.
20 Apr 2015 by Ravi Bhavnani
Yes, it's possible. See this[^] set of articles about steganography.In particular, see Corrina's 19-part series[^] on the subject./ravi
20 Apr 2015 by Sergey Alexandrovich Kryukov
In essence, text as sound already exists: http://en.wikipedia.org/wiki/Morse_code.And you can even shift it to non-audible signal and mix with normal human-perceivable audio. Most certainly, this is far from some optimal solution, but it could give you some ideas. :-) —SA
7 Jul 2015 by OriginalGriff
If you don't understand something complicated, then the place to start is Google: It led me very quickly to this tutorial series: AES (Rijndael) Explained[^] (You tube, four parts)As for the implementation and use, Google again is very helpfull: AES in C[^] provides a lot of resources, some...
27 Oct 2015 by Dzianis Igaravich Leanenka
Hello to everyoneIs anyone able to explain how to create a scheme of a register if I know the polynomial function that describes it?For instance p(x) = x^4 + x + 1How is the scheme look like?Thank you in advance.
24 Nov 2015 by Matt T Heffron
Suggestions, either check for shift being in the range 0 to 25 (or 0 to -25) and requery the user for a valid shift value, or take the shift as modulo 26:shift %= 26;After that, then the shifted letters are no more than 26 out of range, so check for in range and add or subtract 26 as...
11 Feb 2016 by OriginalGriff
You can't. SHA is not an encryption algorithm - it's a hashing algorithm. The difference is that encryption can be reversed, and hashing can't.You are right to use hashing though - but you don't try to "decrypt" it - you store the hashed value and compare the freshly-hashed user input to...
22 May 2016 by RajeshKumar D
Configuring PGP Encryption and Decryption part of MULE ESB
14 Jul 2016 by Foothill
Another possible avenue is to use AES Encryption (msdn link: AES Class)Since AES is symmetric-key encryption, all you need is a passphrase that you can remember and you can encrypt just about anything. You can use a SHA512 hash to generate your crypto keys.This example includes an...
6 Oct 2016 by DRD94
At the moment I am storing my connection strings in my app.config file in plain text. Bad practice, I know, and I am trying to encrypt them instead. I've referred to https://msdn.microsoft.com/en-us/library/ms254494(v=vs.110).aspx and haven't had an issue with getting the app.config part working...
5 May 2017 by OriginalGriff
Decrypt it. Unless you know which bits are the random padding, you can't compare them - and you don't!
12 Jan 2018 by Richard MacCutchan
See Encrypting Data | Microsoft Docs[^]. However, if you are concerned about securing your data then XML is not the best storage choice.
13 Jan 2018 by F-ES Sitecore
Use LegalKeySizes to discover the legal size of your key KeySizes[] sizes = DES.LegalKeySizes; foreach (var s in sizes) { Debug.WriteLine(s.MinSize + " - " + s.MaxSize); } For DES you'll see this is a min and max of 64, ie it has to be 64 bytes, and if you use ASCII characters to build...
13 Jan 2018 by OriginalGriff
Calling Close should call FlushFinalBlock - but the reference sources show that it doesn't specifically override the Close method in the Rfc2898DeriveBytes class, so it might be worth replacing your call to close: using (CryptoStream cs = new CryptoStream(ms, encryptor.CreateEncryptor(),...
15 Mar 2018 by RickZeeland
This CodeProject article describes how to do your own obfuscation, it is in C though, but maybe you will find the utilities useful: Binary Obfuscation[^] You might also find the SecureString class interesting: SecureString Class (System.Security)[^]
15 Mar 2018 by Gerry Schmitz
I would say that a password protected zip / compressed file is the simplest (secure) option. You can compress / decompress in memory.
22 Jul 2018 by OriginalGriff
You can't decrypt a hash at all - that's the whole idea. Hashing is not the same as encryption - it's a one-way process which "throws away" information meaning the original input cannot be regenerated from the output value. For example the simplest hash is to add all the bytes together, and...
29 Oct 2018 by Dave Kreskowiak
NEVER encrypt passwords. ALWAYS hash them instead. Salted Password Hashing - Doing it Right[^]