How to Configure AWS HTTP API Gateway for ECS with HTTPS Listener
5.00/5 (6 votes)
Use Amazon ECS and API Gateway to implement Microservice
Introduction
Amazon Elastic Container Service (Amazon ECS) is a comprehensive container orchestration service designed to streamline the deployment, management, and scaling of containerized applications. On the other hand, Amazon API Gateway is an AWS service tailored for creating, publishing, maintaining, monitoring, and securing REST, HTTP, and WebSocket APIs at any scale. In this article, we will explore the process of implementing a Microservice architecture using Amazon ECS in conjunction with AWS API Gateway.

Create ECS with Application Load Balancer
By default, when you create a VPC (Virtual Private Cloud) in AWS, it sets up four subnets, two of which are public, and two are private. For security reasons, it’s advisable to deploy your ECS (Elastic Container Service) and load balancer in the private subnets.
First, let’s create an Application Load Balancer (ALB). Since it doesn’t need to be publicly accessible, choose the “Internal” type during creation. Select your VPC and ensure you pick the private subnets. Configure an HTTPS listener, making sure to select the correct SSL certificate. In the HTTPS listener settings, set it to forward traffic to a new target group. Create a new target group, choosing IP addresses as the target type and using the HTTP protocol. Don’t forget to specify a health check path. The key here is that the HTTPS listener forwards traffic to an HTTP target group.

Now, when creating an ECS cluster, configure load balancing with the previously created ALB and target group. Ensure that the ECS network security group allows all TCP traffic from the security group associated with the Application Load Balancer.

AWS HTTP Gateway
Next, let’s create an AWS HTTP Gateway. AWS API Gateway offers both REST Gateway and HTTP Gateway options, with HTTP Gateway being the faster and more cost-effective choice. To establish private integrations connecting your HTTP API routes to resources in a VPC, such as Application Load Balancers or Amazon ECS container-based applications, you can use VPC links. VPC links facilitate secure connections between API Gateway and your VPC resources. They are reusable across different routes and APIs.
To set this up:
- Navigate to the API Gateway in the AWS Management Console.
- Select VPC Links and add a VPC Link for HTTP APIs. Choose the VPC and subnets used for your ECS and ALB.

Now, proceed to create an HTTP API. At this stage, you don’t need to add integrations; just provide an API name, leaving everything else at default settings. Once the API is created, add a route for Any -> /{proxy+}. Now, go to Integrations, select Attach integrations to routes, and create and attach an integration. Choose Integration Type as Private Resource, select the integration method manually, and opt for ALB/NLB. In the dropdown list, choose the ALB you created earlier. For the listener, select HTTPS:443 since your ALB has only one HTTPS listener. Finally, select the VPC link you created earlier from the VPC link dropdown list. After attaching the integration, an invoke URL will be generated on the $default stage.

You can now use this invoke URL as the base URL to test your API, e.g., {invoke URL}/health. If you receive a 400 Bad Request — The plain HTTP request was sent to the HTTPS port, it’s because you forgot to set the secured host in your integration.
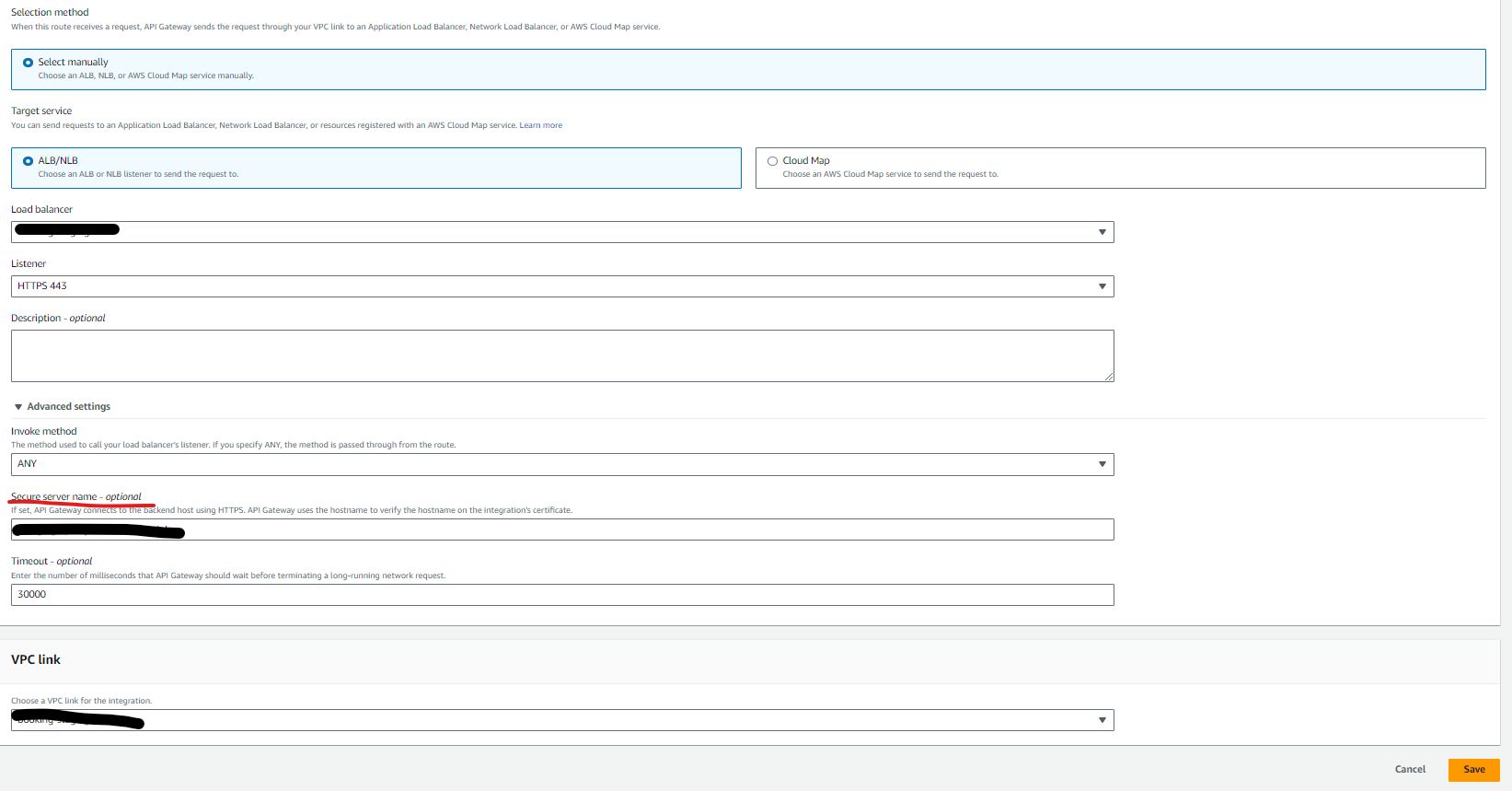
To fix this issue, go to Integrations -> Manage Integrations -> Edit, and select Advanced Settings. The Secure server name field should not be left blank. It should match the domain of the HTTPS certificate on your ALB (Application Load Balancer). Copy the certificate domain to the Secure Server Name field. Now, try {invoke URL}/health again, and it should work seamlessly.
History
- 12th September, 2023: Initial version
