eBPF is a well-known but revolutionary technology—providing programmability, extensibility, and agility. eBPF has been applied to use cases such as denial-of-service protection and observability. Over time, a significant ecosystem of tools, products, and experience has been built up around eBPF. Although support for eBPF was first implemented in the Linux kernel, there has been increasing interest in allowing eBPF to be used on other operating systems and also to extend user-mode services and daemons in addition to just the kernel.
Today we are excited to announce a new Microsoft open source project to make eBPF work on Windows 10 and Windows Server 2016 and later. The ebpf-for-windows project aims to allow developers to use familiar eBPF toolchains and application programming interfaces (APIs) on top of existing versions of Windows. Building on the work of others, this project takes several existing eBPF open source projects and adds the “glue” to make them run on Windows.
We are announcing this now while the project is still relatively early in development because our goal is to work in collaboration with the robust eBPF community to make sure that eBPF works great on Windows, and everywhere else.
Architectural overview
The following diagram illustrates the architecture of this project and related components:
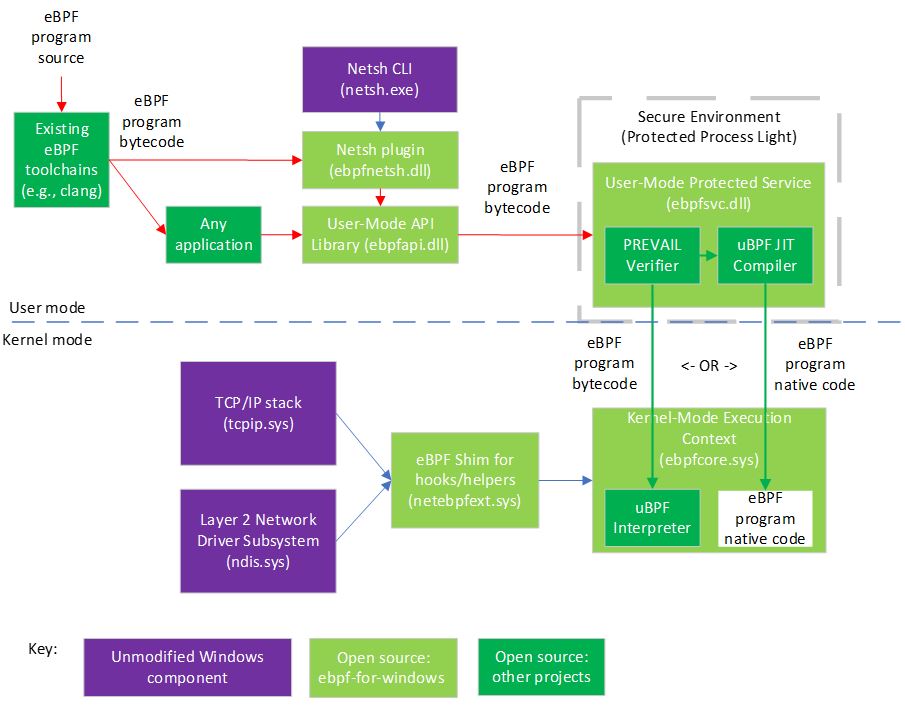
As shown in the diagram, existing eBPF toolchains such as clang can be used to generate eBPF bytecode from source code in various languages. The resulting bytecode can then be used by any application or manually through the Windows netsh command-line tool, both of which use a shared library that exposes Libbpf APIs, though this work is still in progress.
The library sends the eBPF bytecode to a static verifier (the PREVAIL verifier) that is hosted in a user-mode protected process, which is a Windows security environment that allows a kernel component to trust a user-mode daemon signed by a key that it trusts. If the bytecode passes all the verifier’s safety checks, the bytecode can be either loaded into the uBPF interpreter running in a Windows kernel-mode execution context or compiled by the uBPF just-in-time (JIT) compiler and have native code loaded into the kernel-mode execution context.
eBPF programs installed into the kernel-mode execution context can attach to various hooks to handle events and call various helper APIs exposed by the eBPF shim, which internally wraps public Windows kernel APIs, allowing the use of eBPF on existing versions of Windows. So far, two hooks (XDP and socket bind) have been added, and though these are networking-specific hooks, we expect many more hooks and helpers, not just networking-related, will be added over time.
Is this a fork of eBPF?
In short, no.
The eBPF for Windows project leverages existing open source projects, including the IOVisor uBPF project and the PREVAIL verifier, running them on top of Windows by adding the Windows-specific hosting environment for that code.
Does this provide app compatibility with eBPF programs written for Linux?
The intent is to provide source code compatibility for code that uses common hooks and helpers that apply across Operating System ecosystems.
Linux provides many hooks and helpers, some of which are very Linux specific (using Linux internal data structs, for example) that would not be applicable to other platforms. Other hooks and helpers are generically applicable, and the intent is to support them for eBPF programs.
Similarly, the eBPF for Windows project exposes Libbpf APIs to provide source code compatibility for applications that interact with eBPF programs.
Learn more and contribute
The ebpf-for-windows project brings the power of eBPF to Windows users and is intended to eventually reside in a community-governed foundation in the eBPF ecosystem. With your input and help, we can get there.
Reach out to us or create an issue on GitHub. We’re excited to continue to refine and extend ebpf-for-windows so that everyone can benefit from this project. We are eager to see what you discover with this project and how it evolves.
