The post Understanding HTTPS Protocol appeared first on codecompiled.
These days, we see most of the sites using HTTPS protocol for serving the webpages. More commonly, we can see the HTTPS protocol on the sites which contain confidential information such as the websites of banks.
If we go to Google and check the address in the address bar, we will see something as the following address:
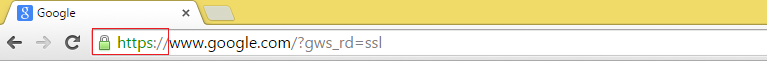
As we can see above, “https” is highlighted in green and lock symbol is displayed before it to indicate that the web page is being requested over the https protocol.
HTTPS is a version of the HTTP protocol used for securely transmitting data between the browser and server.
The communication between the browser and server happens over the HTTP protocol. Client submits information to the server which is sent in an unencrypted form over the network when we use the HTTP protocol.
So if some intruder has access to the physical network through which the browser and the server are communicating, then he will be able to access the information which is being transmitted between the web browser and the web server.
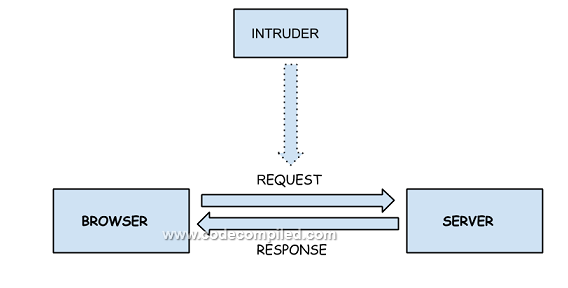
HTTP is fine in many scenarios in which we don’t need much security to encrypt the data. But for applications such as banking applications which send data such as credit card details and other confidential information, this may be a security threat. If there is an intruder watching over the communications channel, he may easily get access to the confidential information provided by the end user.
HTTPS Ensures Secure Communication
To prevent such a security threat, HTTPS is used. HTTPS is a protocol for securing data which is transmitted between the web browser and the web server.
HTTP is HTTP protocol+SSL protocol. SSL is a protocol which provides safe communication over network by encrypting the information. It uses asymmetric cryptography which means that the public key is distributed freely while the private key is available only to the recipient of the message.
HTTPS protocol provides two advantages over the normal HTTP protocol:
- It ensures that the user is communicating with the correct website, the one he intends to communicate and not some intruder.
- It ensures that the contents of the communication between the web browser and the web server are encrypted and hence are not accessible to the intruder.
So in HTTPS, SSL takes care of securing the data being transmitted between the client and the web server.
HTTPS Process
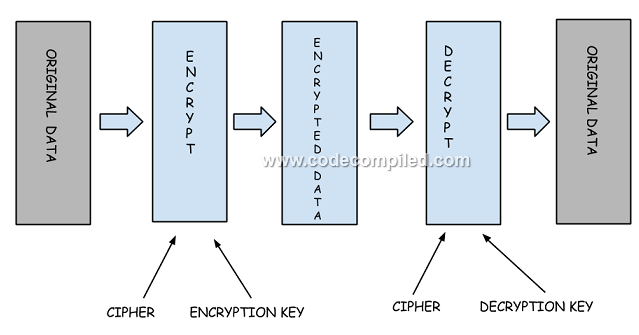
To understand how the HTTPS protocol works, we should understand how the encryption and decryption process works.
Encryption means we transform the text into some other form so that it is non readable by others.
Decryption means that we transform the encrypted text back to the original form.
Encryption and decryption process may also use keys to encrypt and decrypt the information. So if some information is encrypted using a key, then it can be decrypted using the same key. This is called Symmetric key as the same key is used for both encryption and decryption.
If we use one key to encrypt the string and a different key to decrypt the string, then this key is called asymmetric key. The key which we use for encrypting the string is called public key while the key which we use for decrypting the string is called the private key.
So now we understand that HTTPS is used to securely transmit information between the web server and web browser. There is a well defined process which happens while transmitting the information using the HTTPS protocol.
Following process happens when the browser requests a page using the HTTPS protocol.
- Browser makes an https request to the server, server listens on the port 443 which is the port which web servers use to listen for the requests made using the HTTPS protocol.
- Once the connection between the web browser and the web server succeeds, the SSL handshake process happens.
In the handshake process, browser and server agree on things such as which encryption algorithm to use for encrypting the data. So handshake process is agreement between the web browser and web server about how to encrypt the data. Following happens in the handshake process:
- Browser sends a hello message to the server with some details about itself to the web server such as the SSL version it supports.
- Server responds with a similar server hello message which contains details such as the SSL version which will be used for the communication.
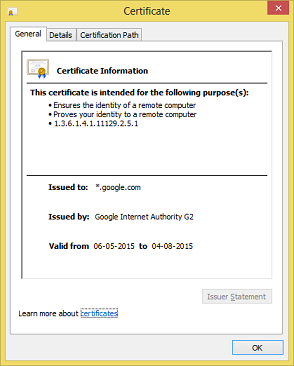
- Web Server sends a certificate to the browser which contains the public key which is used to encrypt the data. Certificate also contains other details such as the issuer of the certificate, validity of the certificate and the server identity. So the browser is ensured that the server is the one it intended to connect.
- Browser verifies the server certificate and sends a certificate verify message to inform the server that the certificate is verified.
- Browser sends a “Change cipher spec command” telling the server that the data which it will send now to the server will be encrypted.
- Server responds with a similar “Change cipher spec command” telling the browser that the data which it will now send to the browser will be encrypted.
If we click the lock symbol in Chrome, we can see the digital certificate sent by the server.
- Browser generates a symmetric key and encrypts it using the public key it got from the server in the certificate. Browser sends this encrypted symmetric key to the server. This symmetric key is used for encryption and decryption for the entire session.
As we know that digital certificate is used to provide the public key. There are two important terms to understand in relation to the digital certificates .
X.509 is a standard used to define the format of the digital certificate such as what information the digital certificate will contain.X.509 certificates includes some of the following information:
- Version: Specifies the X.509 version
- Serial number: The unique number assigned to the certificate for distinguishing the certificate
- Issuer name: This is usually Certification Authority
- Public key: The public key of the certificate
Certification authority or CA is an entity which issues digital certificates.We need to get the digital certificate from the CA.Digital Certificates are signed by the CA which ensures the validity of the certificate.
The post Understanding HTTPS Protocol appeared first on codecompiled.
 General
General  News
News  Suggestion
Suggestion  Question
Question  Bug
Bug  Answer
Answer  Joke
Joke  Praise
Praise  Rant
Rant  Admin
Admin 






